- Jh123x: Blog, Code, Fun and everything in between./
- My Blog Posts and Stories/
- GreyCTF 2023 Qualifiers: ReService/
GreyCTF 2023 Qualifiers: ReService
Table of Contents
This is the author’s writeup for the challenges ReService in the rev category.
This describes the intended solution when I made the challenge.
Challenge Description #
I found this file that was installed by the virus. Can you find out what it does?
It seems to connect to a c2 server and makes use of the current time.
- Junhua
A distributable file called malware is also provided.
My Notes #
- This is mean to be an easy question for golang rev veterans.
- My intended solution is not to actually reverse the binary but to make use of the information provided in the challenge description
- I’ve also consulted my other Rev CTF players to see if it is solvable and it seems like it was quite solvable.
I’ll be going through the fastest solution that does not actually involve reversing.
Notes to future self when setting up this challenge. #
- Do not name a distributable malware
Analyzing the challenge description #
The challenge description mentions that the malware connects to a c2 server and makes use of the current time.
This means that the “malware” connects to some remote server and fetches some information from it.
Analyzing the file #
Instead of using static analysis, I’ll make use of dynamic analysis and check the types of information it collects from the C2 server.
This can be done using wireshark.
By loading up wireshark and running the malware. We can see that the malware connects to the remote server using TCP.
By following the stream, we can get the flag
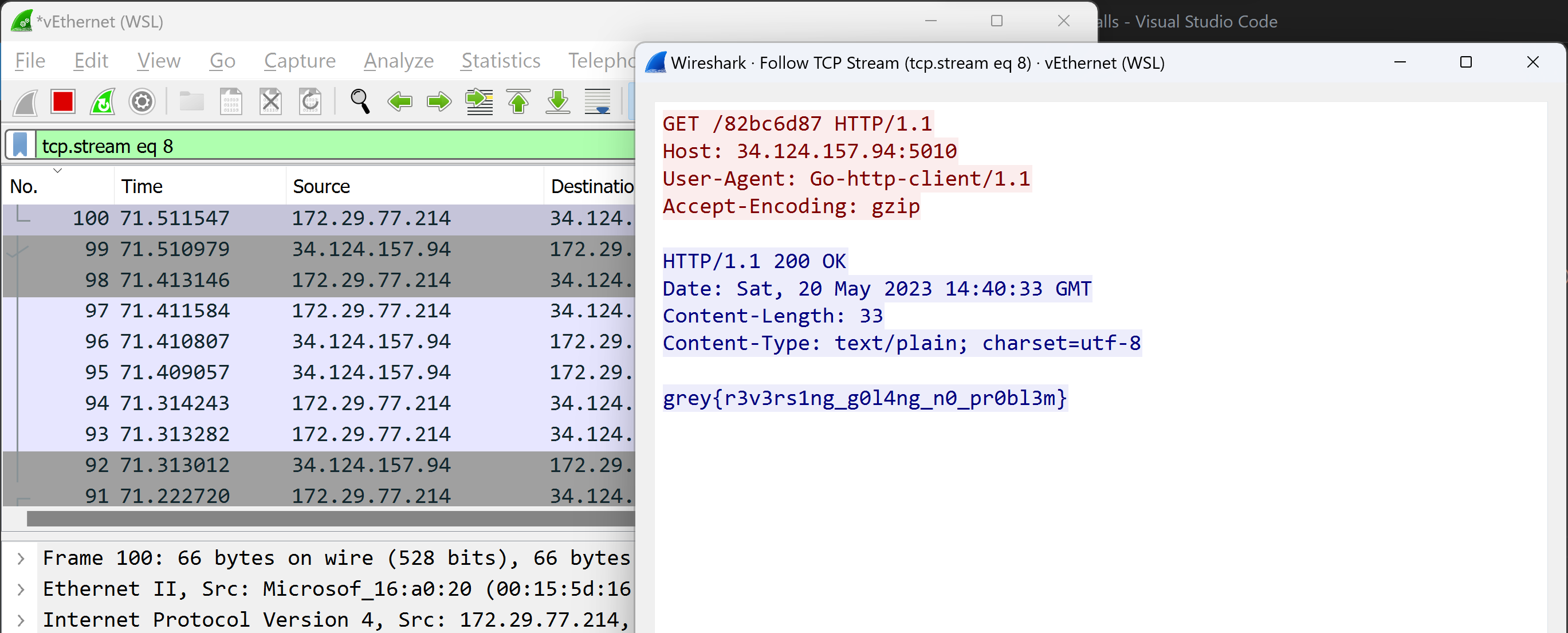
Spoilers for those who are attempting the reverse route #
Below is the original binary for malware
package main
import (
"fmt"
"hash/crc32"
"io/ioutil"
"math/rand"
"net/http"
"strings"
"time"
)
func path_generator() string {
// Generates a random string with time as seed
now := time.Now()
sec := now.Unix()
// Shift slightly
sec >>= 4
// Use time as seed
rand.Seed(sec)
// Generate random hex string and pass it into crc32
crc_val := crc32.ChecksumIEEE([]byte(fmt.Sprintf("%x", rand.Int())))
return fmt.Sprintf("%x", crc_val)
}
func main() {
// Generate a path from base url
base_url := "http://34.124.157.94:5010/"
path := path_generator()
visit := base_url + path
// Visit the website using a get request
resp, err := http.Get(visit)
if err != nil {
fmt.Println(err)
}
// Get response body
body, err := ioutil.ReadAll(resp.Body)
if err != nil {
fmt.Println(err)
}
// Convert Body from bytes to string
str_body := string(body)
isMatch := strings.Contains(str_body, "grey{")
if !isMatch {
fmt.Println("This is not the correct server")
} else {
fmt.Println("Communication complete")
}
}