- Jh123x: Blog, Code, Fun and everything in between./
- My Blog Posts and Stories/
- Learning from job interviews/
Learning from job interviews
Table of Contents
I had a job interview that went terribly recently. The interviewer was very knowledgeable in a wide variety of fields.
Many of the questions he asked me on the spot was not something that was too unexpected. However, I found my self unable to answer them on the spot. Thus, I have decided to summarize the questions below to refresh myself before every interview. I hope this resource helps others in need as well.
Operating Systems #
What are the difference between Processes and Threads? #
| No | Processes | Threads |
|---|---|---|
| 1 | Processes = Any program in execution | Threads = A segment of a process |
| 2 | More time taken to create / terminate | Less time taken to create/terminate |
| 3 | More time taken for context switching | Less time taken to context switch |
| 4 | Have their own address space | Share the same address space |
| 5 | Process switching requires a call to the OS | Thread Switching does not require a call to the OS |
| 6 | One process does not block other processes | 1 Thread can block another thread |
What are the different ways of inter-process communication between them? Which one of them is the fastest? #
Requires synchronizations (Using locks / semaphores) #
- Shared memory (With semaphores)
- The fastest as memory does not have to be copied from 1 part to another
- Pros:
- Very fast communication
- Bidirectional communication
- Resources are saved
- Never blocks
- Can be accessed by multiple programs
- Cons:
- Require concurrency control
- No data protection
- Inconsistency of data occurrences as updates are lost.
- Shared files
Does not require synchronizations #
- Piped (Named and unnamed)
- Framing problem
- Multiple readers can tear the message up
- Multiple writers can overwrite each other
- Framing problem
- Message Queues
- Pros:
- Can be used in a distributed way without any shared variables
- Very easy to implement
- Cons:
- Communication is slower as it takes time to setup communication links between processes
- Pros:
- Sockets (Sync)
- Pros
- They are synchronized
- Cons
- Slower as they go through the OS.
- Can only read/write in a linear fashion
- Blocks
- Pros
- Signals (Async)
- Pros:
- Can happen any time
- Cons:
- Used for only a small amount of information.
- Pros:
Useful links #
What are some scenarios where one would use sockets instead of shared memory? #
Pros of sockets #
- Blocking and non-blocking modes
- No freeing required when using sockets
- No need for synchronization
- Easier to implement for distributed computing
Pros of shared memory #
- Can write in a non-linear fashion
- Never blocks
- Can be accessed by multiple processes
- Fixed memory size
Why sockets instead of shared memory? #
- Easier to implement
- Dealing with linear data
Networking #
What happens when you key a website into a browser? #
- The domain of the site is checked against a DNS Server
- If there is a cache hit, the IP address of the website is returned
- Otherwise
- DNS servers can serve either recursively or iteratively to find the IP address(s) of the domain
- The browser then connects to the IP address of the website and initiates the TCP connection with the webserver
- TCP has a 3 way handshake.
- More details here
- This can be the CDNs that are set up by the webserver or the actual server itself.
- Generally a web request is a
httporhttpsrequest. However, other requests are also acceptedftp://mailto://file://
- If HTTPS is used, a TLS handshake takes place
- Server present the client with their certificate.
- Client verifies the certificate recursively until it reaches a root certificate that is installed on the system and trusted.
- Using the public and private keys of the server, the client and the server shares chooses an exponent (a & b) decides on a common message (g)
- They will then send over (g, g^a mod p, g^b mod p) where p is a large and safe prime number
- They can use it to compute the shared secret (g^ab mod p)
- Every communication from then onwards will be encrypted using the shared secret and a shared scheme (rsa, aes, etc)
- More details here
- TCP has a 3 way handshake.
- The browser then sends a HTTP(S) request to the server to request for the relevant network resources.
- The server processes the request and sends a response to the client.
- The browser receives the response and renders its contents
- Rendering is done using the engines that is used by the browser (IE: v8 for Chromium based browsers)
Useful links #
Why does TCP requires a 4 way handshake to terminate? #
There are 2 ways to terminate a TCP Connection.
- Graceful Connection release
- Abrupt connection release
In this case we are going to talk about the Graceful Connection release.
How does it work?
- The client send a TCP packet with a
FINbit set in the TCP header - The server acknowledges the packet and sends an
ACKpacket back to the client - The server then sends a
FINpacket to the client - The client sends an
ACKto the server
Sometimes the server may send the FIN packet together with the ACK packet for the client FIN packet.
Useful links #
How does the certificate work? #
Before we talk about certificate, lets talk about where it will be used.
During HTTPS, the client and the server will perform a TLS handshake (On top of TCP).
The message includes the following (Versions earlier than TLS 1.3):
- Client Hello
- The client initiates the handshake by sending a “hello” message to the server which includes the TLS version supported by the client, cipher suites and random bytes
- Server hello
- Server replies to the client hello with a server hello, including the Server’s SSL’s certificate, chosen cipher suite and another random string generated by the server
- Authentication
- The client verifies the Server’s SSL certificate.
- Pre-master secret
- The client sends one more random string of bytes.
- This is encrypted with the public key of the server and can only be decrypted by the private key of the server
- The server decrypts the pre-master secret
- Creation of session keys
- Both client and server generates the session keys from the client random, server random and the pre-master secret
- They will arrive at the same result
- Client sends a finished message encrypted with the session key
- Server sends a finished message encrypted with the session key
- After the handshake completes, the client and server will use the session key to encrypt and decrypt all the messages that they send to each other.
During the server hello step, the certificate is sent from the server to the client.
The image below shows the certificate chain.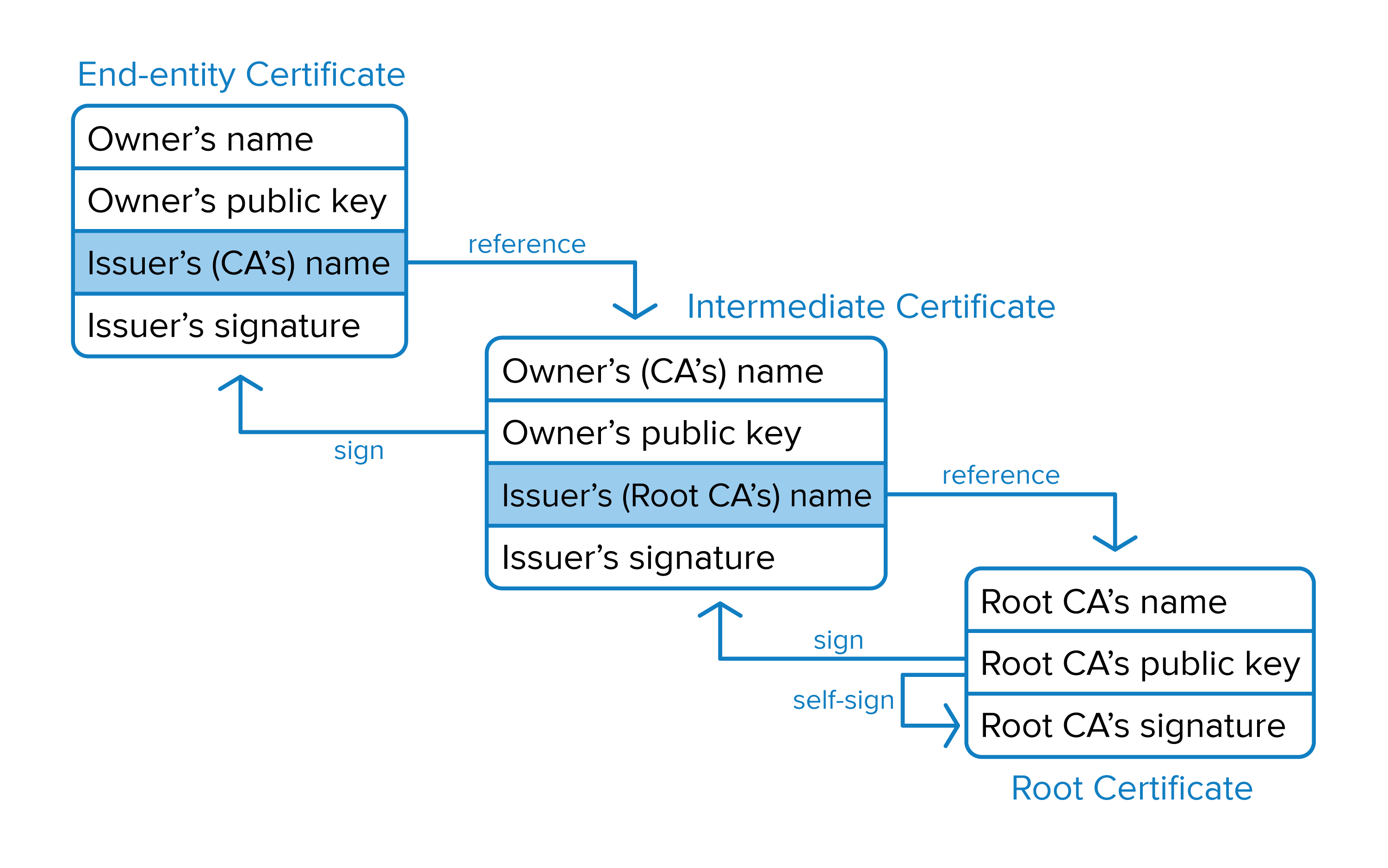
The certificate that is sent by the server is the End-entity certificate which is the certificate that is signed by the Intermediate CA. The Intermediate CA’s certificate is signed by the Root CA. The Root CA is a self signed certificate that is installed on the client’s system and is trusted.
The client will continue to traverse up the certificate tree during the verification process until it reaches a root CA that is installed on the client’s system and is trusted. Otherwise, the connection will be marked as not secure.
Useful link #
Are there any processes that have been done to optimize the handshake? #
HTTP 2.0 #
Pros
- Header compression
- HTTP 2.0 uses a binary framing layer to create a stream for communication.
- During the time of interaction, the TCP connection remains open for the request and response which improves the overall performance
- Multiplexing
- Enables HTTP 2.0 to send multiple network connections over a single TCP connection
- This is made in an asynchronous manner
- This reduces the latency manifold.
- Resource and stream prioritization
- This is a feature that allows essential resources to load first.
- This developers will need to associate dependency levels which allows the clients to consume only the code to that specific webpage.
- Server Push
- This improvement allows servers to send resources to clients before they are requested instead of letting the browser load some HTML to decide what other assets to download
- This pushes assets ahead of time and caches them to improve performance.
Cons
- The HTTP 2.0 Server push is very tricky to implement and integrate into existing applications
- TCP level blocking still caused issues with server loading times
- The concurrent requests used by HTTP 2.0 caused an increase in server load, thus leading to request timeouts
- Clients on a slow network will have their packets gradually dropped, resulting in only a single HTTP 2.0 connection.
- This blocks the loading times of data transfer from the client to the server and the server to the client
Improvements in HTTP 3.0 #
While HTTP 1.1 and HTTP 2 are mainly done over TCP connections, HTTP 3.0 is done over Quick UDP Internet Connections (QUIC). which is a UDP based protocol
QUIC is build on to of UDP and interfaces with HTTP/3 directly. The diagram below illustrates the differences between the 2 protocols.
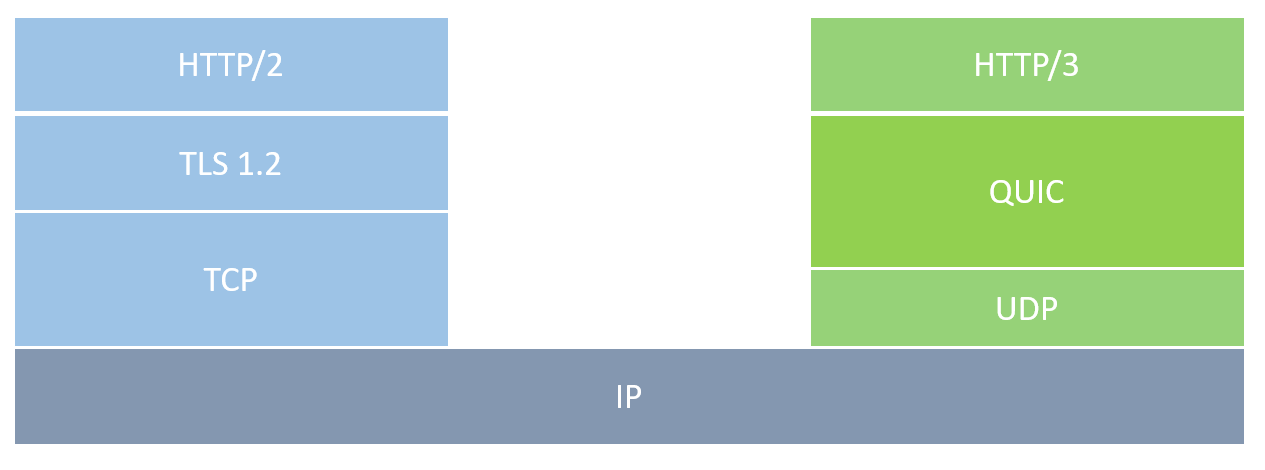
QUIC uses a single handshake to establish a secure connection and the connection is encrypted in the transport layer.
Pros over HTTP 2.0
- QUIC instead of TCP is used
- Has a much quicker hand shake compared to HTTP 2.0
- Encryption by default.
- Decreases the effect of packet loss
- 0 Round trip time
- For servers which clients are already connected to, the client can skip the handshake altogether and start sending data immediately.